A List of The 25 Best Ruby on...
May 8, 2024
Home >> RoR >> How does Ruby on Rails fit into cybersecurity application development?

Quick Summary
As more businesses shift their operations to the internet, safeguarding data and online assets has become crucial. Nowadays, cybersecurity is a need rather than a luxury or an afterthought. A framework called Ruby on Rails (RoR) enables the integration of robust security features right from the start of a company’s development process. This is the best way to make sure that a business is safe. RoR is renowned for being dependable and straightforward to use. It also includes several tools and libraries that ensure your apps are as secure as possible.

It will help you to know that Ruby on Rails is a suitable framework for developing cybersecurity applications when you have decided to create a ruby on rails cyber security application to defend your business from cybercriminals and hackers. It’s common knowledge that Ruby on Rails is a popular framework that is safe by default for creating web apps. Therefore, Ruby on Rails and cybersecurity are the perfect combination to put together if you’re seeking a highly reliable and safe application.
Since RoR is a well-known framework, several security features are integrated to eliminate opportunistic hackers and cybercriminals. Because of its performance, secure operations, and development choices, Ruby on Rails is the platform of choice for most business owners to develop cybersecurity applications. Some notable RoR elements that are beneficial for developing cybersecurity apps are as follows:
One of the main functionalities of Ruby on Rails is that it provides different types of security-based libraries. You can see that developers use these various libraries and gems of Ruby on Rails to create the application which is more secure and same. Nowadays developers use these existing libraries like Devise, Brakeman, and many more to enhance the security of the solution that can be easily launched without any worries.
This feature of Parameter sanitization is very helpful in keeping web applications more secure. The developers define certain parameters while building web apps and other solutions to ensure that only specified users can have access to the information. You will see that developers prefer to use parameter sanitization and validation while building a solution so that it can stay safe from cyber-attacks and there is no risk of data manipulation.
Ruby on Rails has the best security standards to protect your web application against different types of Cross-Site Scripting (XSS) assaults. The developers utilize ROR’s CSRF protection feature to protect all the sensitive information, cookies, and cache against hackers to prevent any type of security breaches. You can use Ruby on Rails for extra security measures because it creates tokens and validates them to provide access to those users only who are making requests from reputable sources.
Should a user interact with the web application, a session will be created specifically for that user. However, the application developers must guarantee that a session created by a specific user will remain exclusive to that user during development. Sometimes, while a user is in the middle of a session on an unsecured website or network, hackers, and scammers will utilize a technique known as session hijacking to seize control of the user.
Conversely, Ruby on Rails provides a robust session management framework that makes safe and encrypted cookie storage possible. By thwarting these two kinds of attacks, Rails’s session hijacking and tampering protection features enhance the application’s overall security.
Hackers cannot obtain user data or information from the cache and cookies thanks to Ruby on Rails’ secure cookie management mechanism. You won’t have to worry about something happening because of this. The cookies’ session data and user information will be password-encrypted to prevent unwanted access and manipulation. Furthermore, adding a secure flag to cookies enhances the application’s security. As a result, web browsers will not send cookies in connection with HTTP requests
One feature that can be added to Ruby on Rails is active record protection. It can enable application-level encryption, which adds another degree of security to the application’s features. There are several advantages to using Active Record encryption, but the primary one is that it protects sensitive data and personal information related to your application. This process involves the encryption and decryption of user data and the application between the database and the application. This process is carried out whenever it is required.
When creating a secure Ruby on Rails application for cybersecurity, you have many security testing tools at your disposal. Developers can find security flaws and vulnerabilities in the code database more quickly using security tools like Brakeman. Using security technologies can help protect against SQL injection, cross-site request forgery attacks, and logging vulnerabilities. Including the necessary security testing tools within the cybersecurity application design process will enhance the overall security posture.
Although session-based authentication is also present in Ruby on Rails, token-based authentication is more commonly utilized. Most web applications use authentication tokens to confirm that the person attempting to access or use the program is legitimate. Every time a user interacts with any feature or component of the app, the authentication token is generated for each user or session. It is then validated or confirmed to verify the authenticity of the user’s actions. The duration of these encrypted tokens is flexible and can be changed or disabled at any time, independent of the situation. This innovation will strengthen the application’s security and make it more difficult for spammers to execute spoofing attacks.
“Top 10 Reasons Why Use Ruby on Rails for eCommerce Project? “
– Also Read Article
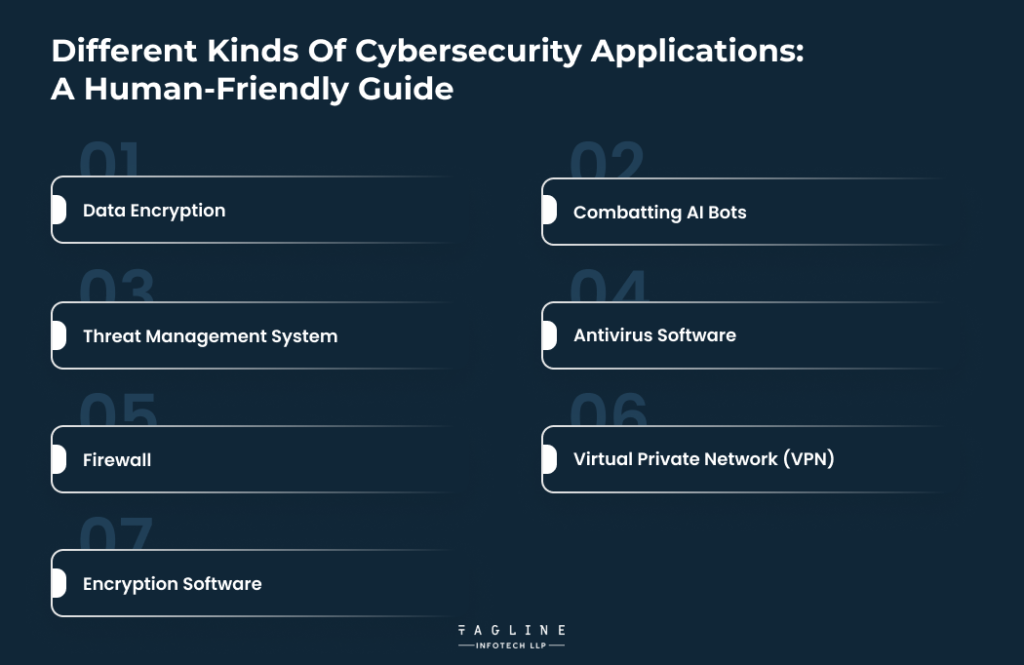
In today’s primarily digital world, cybersecurity is a multifaceted endeavor encompassing a range of technologies intended to protect networks, systems, and data. It goes beyond simply creating a secure password. Now that the technicalities have been eliminated let’s explore the various cybersecurity tools that are currently accessible, presented in a language that even your grandma might understand!
Ruby on Rails is also used to build different types of data encryption cyber security apps. In these apps, users can easily convert their information into encoded text so that hackers can’t read your personal information without the decryption key. Nowadays importance of different types of data encryption apps is a lot because they keep hackers away during data transmission and storage processes without revealing any data.
You will see that since the rise of AI, many AI bots are in the market that are used for cyber-attacks. The main purpose of these bots is to create fake traffic on a website or app through multiple devices to crash the whole web server. To prevent these attacks, developers created combatting AI bots that counterattack AI bots to log them out by creating multiple sessions.
You can see that a threat management system is a type of cyber security application that is mainly used to identify the vulnerabilities of the website or app that hackers may use. After identifying these vulnerabilities this management system helps to fix all the defects to improve the overall security of the solution.
Imagine your computer as though it were your physical form. In the same manner that you receive a flu shot to prevent illness, antivirus software functions similarly to a digital flu vaccine for your computer. This software operates by scanning your computer for potentially dangerous software, sometimes known as “malware,” and removing it before it can compromise your system.
Think about a firewall as the high-end, private club’s security officer. Its purpose is to determine who is permitted entry and who is not. The firewall on your personal computer monitors all incoming and outgoing traffic to ensure that only secure data can flow through. If anything or anyone questionable tries to enter, the firewall will stop it dead at the door.
Consider yourself Harry Potter, donning an invisible cloak to protect yourself from the bad guys. With a virtual private network (VPN), your online activity is effectively hidden from prying eyes—like an invisible cloak. Your internet protocol (IP) address can be hidden, which makes it very difficult to trace your online activity.
Remember those cereal boxes with the decoder rings on them? Do you remember any childhood secret languages you may have created? With encryption software, your data is converted into a secret code. If someone tries to access it without the ‘key,’ they will find a disorganized mess instead of information that can help them.

Because of how interconnected the current world is, cybersecurity is not just a buzzword but a necessity. Individuals, companies, and governmental organizations use various applications to manage their financial transactions, personal data, and other facets of their identity. These apps bring many challenges across the cybersecurity area, even though they offer convenience and operational efficiency never seen before. The most significant app security obstacles that users, administrators, and developers face are enumerated below.
The instruments and tactics used by cybercriminals also evolve with the advancement of technology. Keeping up with the quick speed at which technology develops is one of the biggest problems facing people today. Hackers start planning ways to undermine new security features as soon as they are implemented. It resembles a race against the hands of time. It is vital to watch for potential security threats and constantly keep up with this dynamic evolution.
These days, apps aren’t standalone products; they usually integrate with other elements, such as databases and outside services. Although this link offers excellent functionality, it also creates several entry points that hostile actors could use to launch assaults. Comprehensive expertise and an all-encompassing approach are needed to manage the security of such advanced systems and account for all potential hazards.
The human element is often among the weakest links in any cybersecurity chain. Human error can make even the most secure systems vulnerable to security breaches, whether by using weak passwords, falling for phishing operations, or inadvertently downloading malware. It will always be necessary to educate end users on the best practices for cybersecurity.
A company’s cybersecurity procedures must be scalable to match the company’s expansion. A large organization with thousands of employees may find that more than what worked for a small group of ten people is required. Scaling security measures without compromising effectiveness or customer experience quality is a challenge many enterprises face.
Embrace the cybersecurity prowess of Ruby on Rails for robust and secure development!
Hire Ruby on Rails Developer to protect your applications and establish a secure foundation for your projects.
Ruby on Rails has the potential to provide you with several Ruby on Rails gems or tools that will enable you to fortify the security controls you have put in place for your cybersecurity application. With the help of these amazing RoR gems, you can build a strong defense against hackers and cyber thieves and check the cybersecurity program for any flaws or vulnerabilities. The following are a few gems that you may apply in Rails to enhance the security application’s performance:
The Devise authentication library is one popular authentication library that can help you ensure your authentication methods are secure. In addition to enhancing the application’s cybersecurity capabilities, it offers a wide range of features for seamless user authentication, including the capacity to lock out an account after a predetermined number of unsuccessful login attempts, password hashing and salting, password recovery capabilities, and two-factor authentication.
The CanCanCan authorization library aims to let developers construct fine-grained permission management and role-based access control systems. You may create adequate permission levels to access specific data and information with the help of this RoR library, which will stop unauthorized hackers from accessing sensitive capabilities.
Brakeman is a security tool that does static analysis to help you examine and verify that your cybersecurity application’s code database is free of security flaws. With Brakeman’s assistance, you may defend the application against flaws like SQL injection, cross-site scripting, and others. Furthermore, Brakeman offers thorough reports and repair recommendations, making it much easier to identify and take care of security issues in their early phases.
Get in touch with us at Ruby on Rails Development Company for further inquiries or to explore how our Ruby on Rails development expertise can benefit your company. In addition to making it easy to develop scalable and trustworthy apps, the Ruby on Rails framework provides many features that may be leveraged to enhance cybersecurity. With its vast collection of security-focused gems and built-in security techniques, Rails offers developers a comprehensive arsenal for creating secure applications.
In the current climate, when cyber dangers are ever-present, dedicating time and resources to cybersecurity is not only a wise decision but also a need. This procedure is made more accessible and efficient using Ruby on Rails, allowing companies to focus on innovation and expansion without compromising security.
Yes, Ruby on Rails is a preferable high-level programming language that can be used to build cybersecurity app. It can be used to build different types of tools like network security testing, automated testing, and many more.
There are some of the most popular Ruby on Rails security gems like Brakeman, Dawnscanner, Rail Roader, OWASP ESAPI Ruby, and many more that can be used to create secure apps.

Digital Valley, 423, Apple Square, beside Lajamni Chowk, Mota Varachha, Surat, Gujarat 394101
+91 9913 808 2851133 Sampley Ln Leander, Texas, 78641
52 Godalming Avenue, wallington, London - SM6 8NW