Role of Python Libraries in Image Processing
October 30, 2025
Home >> Cloud Computing >> 15 Must-Know Challenges in Hybrid Cloud Security

Quick Summary
In the modern digital era, organizations utilizing cloud technologies increasingly prioritize security, with a significant 94% highlighting it as their main concern. This issue becomes even more pronounced for businesses adopting hybrid cloud models, where 58% acknowledge the intricacies involved. Hybrid cloud setups allow for the distribution of workloads across diverse environments such as private clouds, on-premises servers, and public clouds providing exceptional flexibility. However, this adaptability introduces additional challenges and potential vulnerabilities.
Poor configuration management is one of the major challenges and encourages many risks of unauthorized access. Coupled with this, contradictions between network policies pose an additional challenge. All these factors make managing hybrid cloud security an uphill battle for most organizations. The financial impact of security breaches can also be very heavy. According to different estimates, the average cost of an incident is around $3.92 million.
This blog post will present the common challenges that affect hybrid cloud security and identify the best strategies for implementation against such vulnerabilities.
Hybrid cloud architecture brings together private and public cloud services into a unified system, making management and operations more straightforward. By leveraging advanced software, organizations can easily move workloads between their physical data centers and public cloud networks.
Many businesses incorporate Infrastructure as a Service (IaaS) platforms like Microsoft Azure, Google Cloud, and AWS into their hybrid setups. While this model provides significant benefits in terms of scalability and flexibility, it also introduces unique challenges. Security concerns and the complexities of data management and integration can create hurdles that organizations need to navigate carefully to maintain a robust hybrid cloud infrastructure.
Organizations, ever under innovation, are breaking loose from the conventional cloud computing service models into newer options best suited to their needs. The National Institute of Standards and Technology (NIST) defines several main cloud service models as underlining the core of today’s cloud technology:
These service models help organizations maximize their benefits from cloud computing while addressing their unique operational challenges effectively.
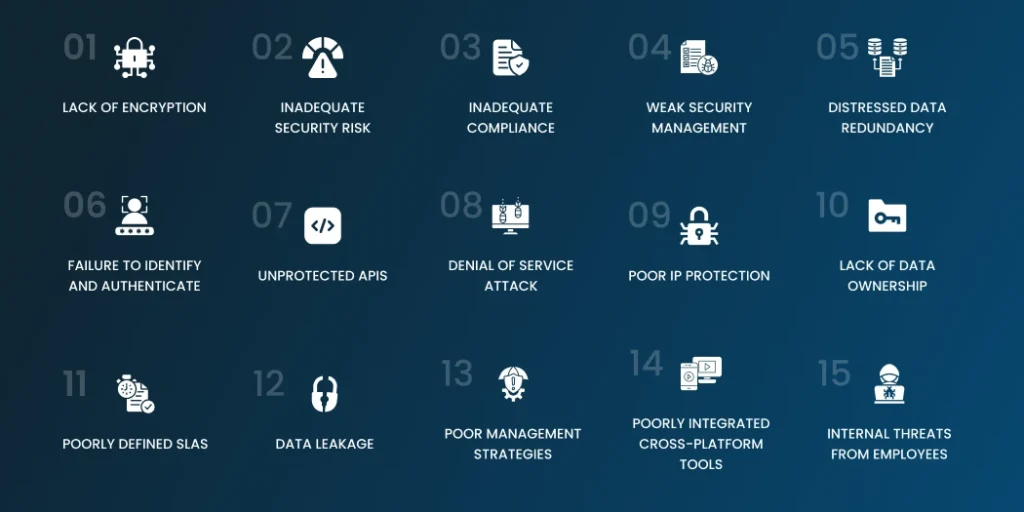
Hybrid cloud environments will pose some security challenges that the organizations need to face:
To address these challenges, organizations should implement a comprehensive cloud computing strategy that incorporates modern technologies and promotes collaboration between IT and security teams.
The National Institute of Standards and Technology defines four key cloud deployment models which vary by matching various business needs and security considerations: the public cloud, private cloud, community cloud, and hybrid cloud.
Each of these cloud deployment models offers different advantages, affording an organization the right choice for its operational and security needs.
Effectively managing a hybrid cloud environment involves understanding both technical and operational aspects. Here are some crucial factors to keep in mind:
By considering these elements, organizations can optimize their hybrid cloud management for better performance and security.
Hybrid cloud systems allow organizations to balance their applications between on-premises and cloud platforms, offering valuable flexibility. However, they also introduce significant security challenges that must be addressed. Protecting data is essential, as it is the foundation of any business, and breaches can lead to serious consequences.
Proper management of access rights and adequate protection of data can be two of the major elements in a hybrid cloud strategy toward security. Additionally, rules and regulations for both data and cloud governance may become increasingly difficult if one has to consider hybrid environments. Because part of the data will be located on cloud servers, organizations must learn to place their trust in their chosen cloud service providers to implement and maintain adequate security. For organizations to successfully deploy hybrid cloud infrastructure, clear protocols must be established, and close communication with their service providers to ensure that all standards of security are met.
As the adoption of hybrid cloud infrastructures continues to rise, with 72% of organizations utilizing this model, the associated security challenges are becoming increasingly critical. Here are some key insights:
Traditional security tools, designed primarily for on-premises environments, often hinder effective security implementation in hybrid cloud settings. A significant 96% of IT and security leaders recognize that hybrid cloud security is a shared responsibility. However, 52% of board members lack a clear understanding of this shared responsibility model.
Experts predict a rise in cybersecurity threats related to cloud technology, with 93% anticipating an increase in attacks in the coming year. Since 2022, a staggering 90% of organizations have experienced at least one cyber intrusion.
The Zero Trust approach is gaining momentum, with 96% of leaders highlighting its importance in strengthening security measures. Additionally, 97% acknowledge that deep observability is essential for tackling hybrid cloud security challenges.
IT and security teams need to align their perceptions of hybrid cloud security with the current security landscape. The effort to enhance hybrid cloud security and address security blind spots is ongoing, making visibility a critical focus area.
To boost the reliability and security of your hybrid cloud setup, it’s vital to protect virtualized data centers and containerized environments. Ignoring even minor issues in hybrid cloud security can lead to vulnerabilities and potential data breaches, particularly when compliance with data privacy regulations is essential.
Integrating hybrid cloud security into DevOps processes allows for automated protection of physical, virtual, and cloud workloads. Solutions like Trend Micro™ Deep Security™ provide a centralized dashboard that offers visibility across various platforms, such as AWS and Azure. This simplifies management, streamlines deployments, and defends against advanced threats like ransomware and network vulnerabilities.
Data transmitted over networks is vulnerable to eavesdropping and man-in-the-middle attacks, where attackers impersonate trusted endpoints. These threats pose serious challenges for hybrid cloud security. To combat these risks, enterprise mobility managers must prioritize the encryption of both communications and data.
Some of the effective solutions are as follows:
Taking these steps would, therefore, increase the security of an organization’s hybrid cloud environment and prevent sensitive information from threats.
Network administrators often struggle to detect and prevent attacks due to insufficient risk profiling of their IT systems. This lack of comprehensive understanding can jeopardize security in hybrid cloud environments, making it challenging to identify and mitigate threats.
A few effective strategies that improve security include:
By using such approaches, organizations can enhance the security of their hybrid cloud environment and prepare to handle possible threats.
Managing compliance in hybrid cloud environments is crucial, especially as data transitions between public and private clouds. Maintaining security while adhering to regulations can become quite complex.
Here are some effective solutions:
By establishing clear compliance across both cloud environments, organizations can minimize risks and steer clear of regulatory pitfalls.
Many organizations struggle with hybrid cloud security due to inadequate identity management and authentication practices across their private and public clouds.
Here are some potential solutions:
By addressing these issues, organizations can significantly improve their security posture in hybrid cloud environments.
Insufficient redundancy in hybrid cloud environments can put a company at risk, particularly if data isn’t effectively spread across various data centers. This can heighten the chances of disruptions and data loss.
Here are some answers on how to achieve redundancy:
These strategies would help organizations prevent vulnerabilities and strengthen the resilience of data within a hybrid cloud setting.
A hybrid cloud environment must be secured, most especially a mix of both the public and private clouds. Both the cloud provider and the organization share a joint responsibility for cybersecurity.
Some successful strategies:
Unsecured API endpoints open the vulnerability of sensitive data to attacks in which the attacker manipulates the token for authentication to gain unauthorized entry to private information. This is alarming in enterprise mobility and BYOD over an unsecured network.
Some of the solutions recommended are as follows:
By addressing these issues, organizations can strengthen their hybrid cloud security and better protect sensitive information.
A Denial of Service (DoS) attack disrupts cloud or mobile services by flooding shared resources, such as CPU, RAM, or network bandwidth. Poor management of cloud resources can hinder access to services, leading to unwanted downtime.
Here are some effective solutions:
The incidence and impact of DDoS attacks targeting both volumetric and application layers are significantly increasing compared to traditional DoS attacks. These attacks utilize multiple sources to inundate networks with traffic, disrupting the normal operation of websites.
To combat DDoS attacks effectively:
By implementing these strategies, organizations can strengthen their defenses against DoS and DDoS attacks, ensuring reliable service availability.
Protecting intellectual property (IP) is critical, requiring strong encryption and authentication measures. IP must be carefully identified, classified, and assessed for any vulnerabilities to ensure its safety.
Effective strategies for safeguarding IP:
When working with cloud vendors, businesses often lose some control over their data once it’s deployed to the cloud. It’s vital to ensure that vendors meet proper security standards and have clear ownership policies.
Solutions to maintain control:
By focusing on these solutions, businesses can better protect their intellectual property and maintain control over their data in cloud environments.
When moving data to the cloud, companies lose some control and must depend on service providers for security, particularly with public cloud systems. A poorly structured Service Level Agreement (SLA) can lead to unexpected challenges in maintaining hybrid cloud security.
To avoid issues, consider these solutions:
Inadequate protocols from cloud providers can lead to data being corrupted, exposed, or improperly accessed especially in environments with Bring Your Device (BYOD) policies.
To protect against data leakage:
These strategies will help companies create strong SLAs and mitigate the risk of data leakage in hybrid cloud setups.
Managing hybrid cloud environments requires a clear plan with defined goals, roles, and policies. Without a structured approach, networks become vulnerable to cyberattacks. An effective strategy is essential to secure hybrid infrastructure and reduce cloud security risks.
Key solutions:
Managing hybrid clouds often becomes inefficient due to the lack of proper cross-platform tools. Security challenges arise when systems aren’t well integrated, leading to vulnerabilities.
Effective solutions:
Internal threats are often overlooked but can be one of the most damaging risks to hybrid cloud security. Malicious employees or insiders may misuse sensitive data to cause harm to the organization.
Ways to mitigate this risk:
These strategies can help organizations better manage hybrid cloud security and address internal and external risks.
No surprise! Many organizations are moving to cloud computing, drawn by its scalability and potential for growth. Minor security concerns often take a backseat when weighed against these benefits. However, managing hybrid cloud security is crucial for organizations that balance on-premise and cloud infrastructure. Companies must adopt protective measures to address these security challenges. Examples include establishing secure tunnels between their networks and the cloud, encrypting sensitive data before storage, and deploying firewalls with basic access control rules. These strategies enhance hybrid cloud security while enabling organizations to leverage the flexibility and scalability of cloud solutions.
To strengthen your hybrid cloud security effectively and with precision, partnering with a company like Tagline Infotech is the best approach. We offer cloud consulting services with deep expertise in security and compliance.
Hybrid cloud security protects data as it moves between private and public cloud environments, ensuring visibility, encryption, and access control.
Secures data, systems, and applications across on-prem and cloud environments by using consistent security measures and monitoring.
Hybrid controls combine automated security tools with human oversight, creating a balanced defense against cyber threats.

Digital Valley, 423, Apple Square, beside Lajamni Chowk, Mota Varachha, Surat, Gujarat 394101
D-401, titanium city center, 100 feet anand nagar road, Ahmedabad-380015
+91 9913 808 2851133 Sampley Ln Leander, Texas, 78641
52 Godalming Avenue, wallington, London - SM6 8NW