Finance & IT Email Marketing: A Data-Driven Approach
February 2, 2026
Home >> Node.JS >> Authenticating REST APIs: 5 fundamental strategies

Application Programming Interfaces (APIs) are the subject of widespread hype. It provides a software interface that makes it easier for two applications to interact, which is essential for scalability and reusability. Here you can see different types of Rest API authentication best practices that can be implemented in the app. Public APIs are increasingly a typical feature of proprietary web apps and services. They can be used by other developers to swiftly combine functions like performance tracking, social media logins, and credit card debts.
Representational State Transfer (REST) is the protocol that they utilise for this, and it integrates seamlessly with Node.js development methods. As a result of this level of interoperability, creating a Node js REST API is a no-brainer. This blog will further lead you to answer your question- ‘how to build an api’
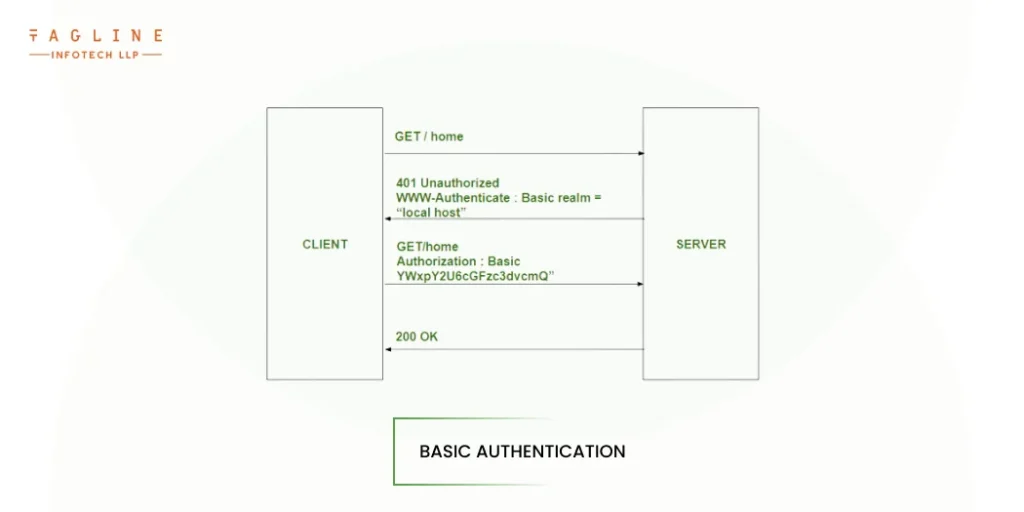
Basic authentication is an HTTP-based authentication method that is the most straightforward way to secure nodejs REST APIs. It encodes usernames and passwords using the Base64 format, which is stored in the HTTP header. When the priority is for an application to remain lightweight and simple, this is an effective method for setting up various API access credentials. However, this approach does not support multifactor authentication (MFA) or dynamic, user-specific credentials out of the box, which would necessitate the use of additional browser-based extensions and authorization tooling.
Basic authentication is widely supported across development toolchains, technologies, and platforms due to its simplicity. One of the major issues with this authentication scheme is that sensitive credentials frequently travel between systems unencrypted. Because threat actors can intercept traffic moving through unsecured channels and steal credentials, using Secure Sockets Layer (SSL) and Transport Layer Security (TLS) channels is a must when sharing sensitive data between multiple web applications, particularly third-party applications. This is by far the easiest way to answer ‘how to create an api’.
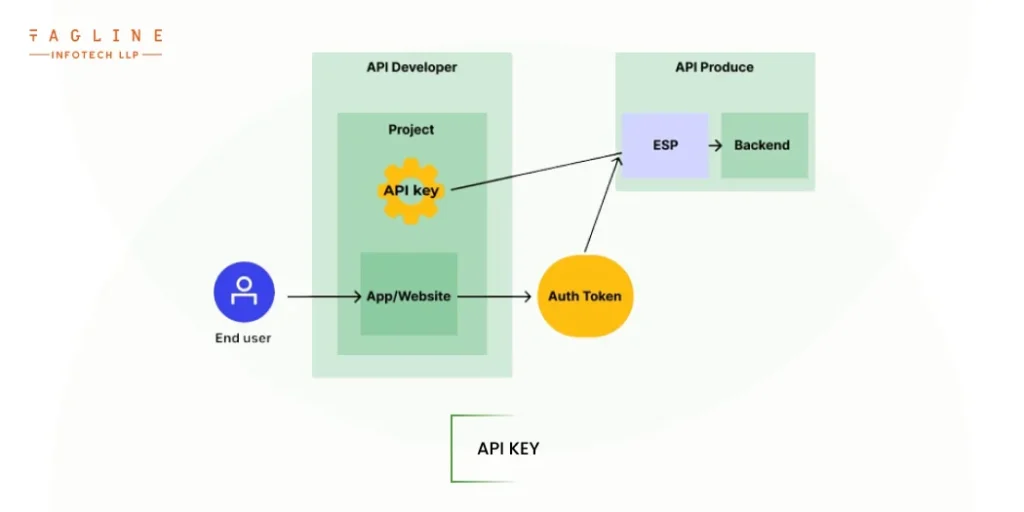
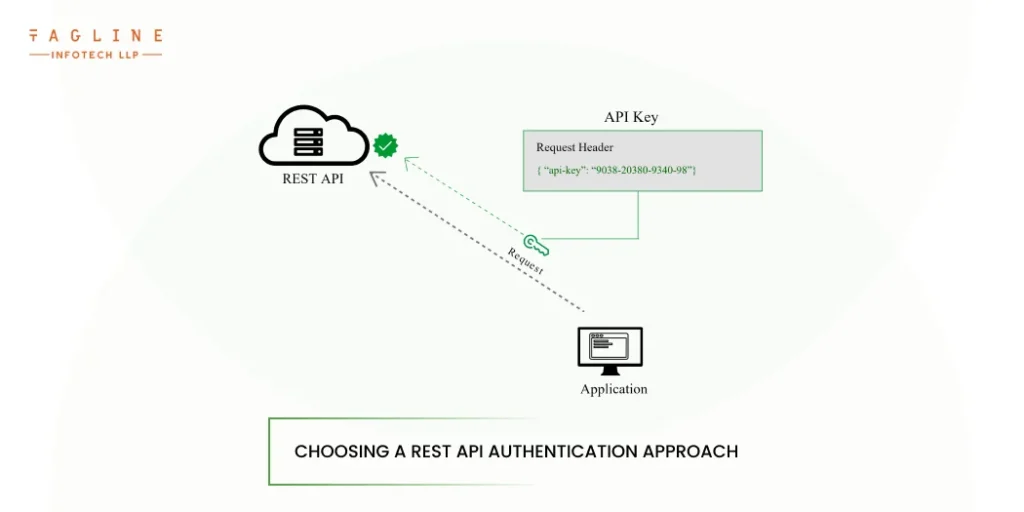
The API keys strategy is a twist on the HTTP Basic authentication strategy. This method generates unique pairs of identifying credentials and API access tokens using machine-generated strings. It is one of the best API authentication methods that you can use. API keys are suitable for consumer-facing web applications because they can be sent as part of the payload, HTTP headers, or query string.
API keys have the advantage of decoupling nodejs API access from the required credentials and validation tokens. Those credentials and tokens can be revoked and reissued as needed, for example, if a user’s permission level changes or there is reason to suspect that the information has been compromised. Unfortunately, API keys are vulnerable to the same risks as basic authentication in that hackers can intercept and exploit the credentials associated with them.
While they do provide a unique identification mechanism for front-end user interactions, allowing them to apply and revoke credentials on the fly, the simplicity of their design limits their ability to support layered authentication or MFA.
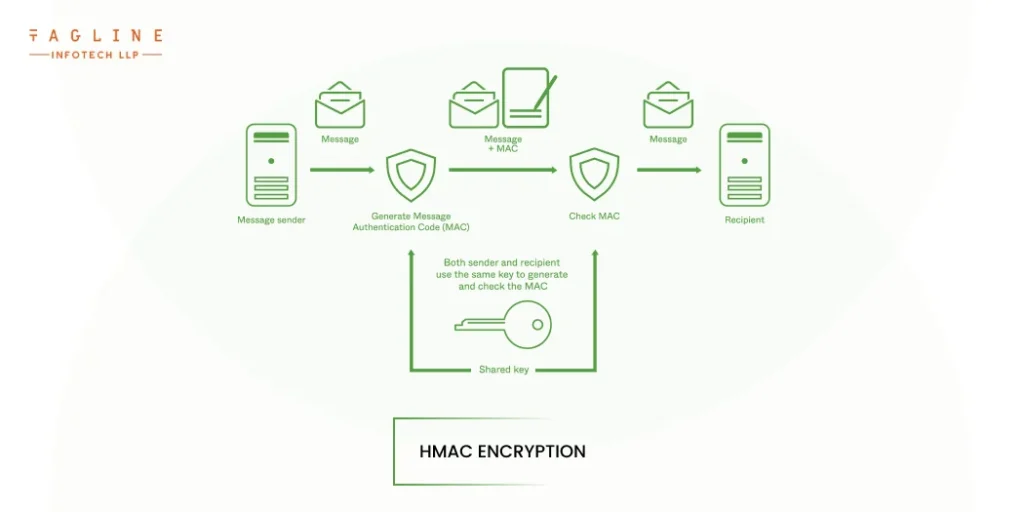
When the integrity of the nodejs REST API’s data payload is a priority, another type of REST API authentication known as hash-based message authentication code (HMAC) is frequently used. HMAC determines the hashing of a REST API’s data payload using symmetric encryption, also known as single-key encryption. It then generates a one-of-a-kind code associated with that hashing and attaches it to the appropriate messages. The key will be shared by the caller and receiver in order to ensure the integrity of the data within the payload.
To illustrate, consider the following basic example of HMAC authentication:
A developer wants URL addresses to expire after a certain period of time in order to provide access to REST API data.
The URL contains the session duration and expiration timestamp, which are signed with an HMAC encryption key.
The encryption key embedded within the URL address is used by the client-server calling the nodejs API to validate the data payload. After the specified time limit has passed, both the client and the server will mark the URL as expired.
If the client or server detects any unexpected changes to the URL or receives a message that uses a previously expired URL, it will notify the API of a key signature mismatch and prompt it to perform a key signature check.
The HMAC approach to REST API authentication requires minimal management and tooling overhead. It’s useful in situations where you have direct control over both the client and server applications. However, when dealing with mobile and web applications that are not under your control, it can be difficult to store encryption keys securely.
A mobile application, for example, that uses URL-based HMAC encryption keys to facilitate data requests is a vulnerable target for attacks, especially if those encryption keys do not have a fixed expiration date. If a threat actor obtains that one-of-a-kind key, he or she can easily coerce the application to accept a malicious data payload by embedding the stolen encryption code within the URL.
“What’s New In The Latest Version Of Node.js 19? Nodejs update version and Features”
– Also Read Article
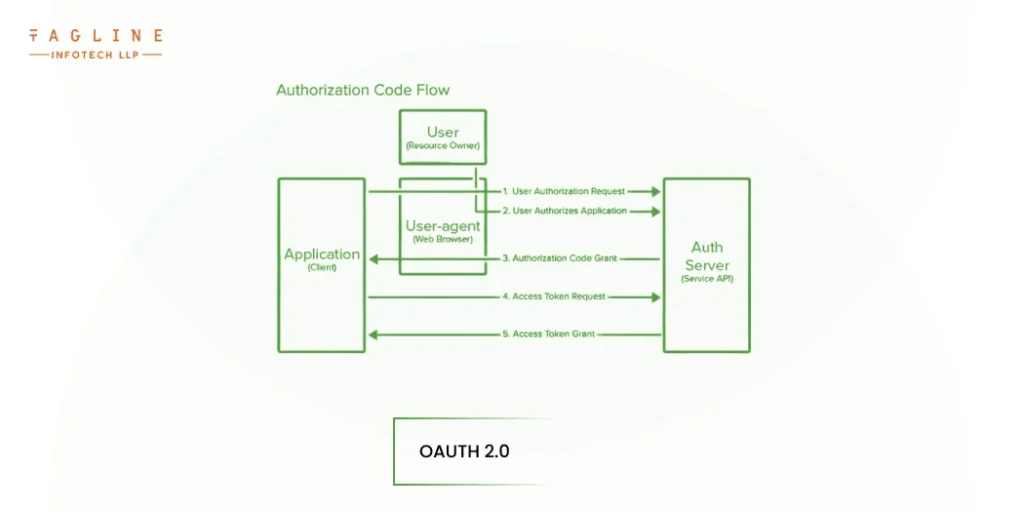
When it comes to REST API authentication or how to create an api, OAuth (specifically, OAuth 2.0) is considered the gold standard, particularly in enterprise scenarios involving sophisticated web and mobile applications. OAuth 2.0 allows for dynamic user collections, permission levels, scope parameters, and data types. Go through this process if you are wondering how to authenticate Rest API for your application. It is the preferred method for organisations seeking to secure a large number of REST APIs containing sensitive information.
OAuth 2.0 generates secure access tokens that are refreshed on a regular basis by employing a set of procedural verification protocols known as grant types. These grant types serve as proxy authentication mechanisms, directing the flow of API access requests while keeping the underlying credentials, tokens, and other authentication information private.
OAuth 2.0 has five major grant types:
· Authorization Code
· Proof Key for Code Exchange (PKCE)
· Client Credentials
· Device Code
· Refresh Token
OAuth supports the concept of scopes, which is a method of limiting an application’s access to a user’s account and associated credentials, in addition to recycling access keys. This allows you to limit how much third-party applications can access a user’s account data. Another benefit of this approach is the ability to define multiple scopes and issue distinct tokens for various types of requests and permission levels.
OAuth can perform payload integrity checks using a JSON Web Token (JWT) in a manner similar to the HMAC authentication approach discussed in the previous section. JWT tokens securely store encrypted, user-specific data and then transfer that data as needed between applications. Because these web tokens can be signed, they can be imbued with new user roles and permissions. Tokens can easily be invalidated or recycled as needed.
Including a shared symmetric key across application services can assist all participating services in concurrently verifying the integrity of the token rather than through a series of validation checks. This reduces the possibility of a single point of failure in the validation process. However, as described in previous sections, managing the distribution of symmetric keys required for payload integrity verification is a daunting security challenge in dynamic, highly scalable application environments.
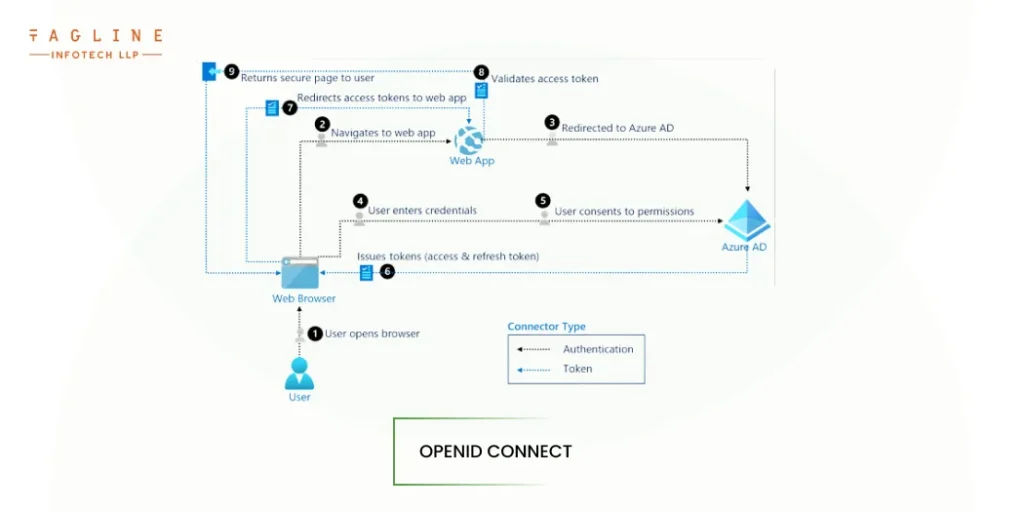
OpenID Connect is an open authentication protocol based on OAuth 2.0. It enables a client application, known as a relying party (RP), to validate a user’s identity in a straightforward manner. This single standard simplifies information sharing by eliminating the need for explicit credential management for third-party applications.
Once users have been authenticated by the RP, the REST APIs covered by OpenID Connect become usable. Finally, the nodejs API associated with that RP can validate using its own variant of the aforementioned OAuth grant types. These are the grant types:
· Authorization Code
· Implicit
· Hybrid
While OpenID Connect is always under the control of the API provider, multiple RPs can use these grant types independently as needed. This approach is ideal for REST API providers who cannot support the complexity of dynamic, enterprise-level credential management tooling but must securely share user data across a wide range of third-party web applications.
Given the variety of REST API authentication approaches, carefully weigh the benefits and drawbacks of each against your specific application requirements before implementing one. Basic authentication’s HTTP-focused approach is great for restricting public access to low-risk data and resources, but it still requires some level of security controls. Meanwhile, API keys are useful in situations where API providers need to identify individual users and control their permissions as necessary.
The sensitivity of data is, of course, an important consideration in the decision. While HMAC provides adequate data payload integrity support for relatively simple operations, OAuth is better suited for complex use cases involving rotating access tokens and adjustable permission levels. For those in the middle, OpenID strikes a good balance between the dynamic access management of OAuth and the simplicity of HMAC.
Whatever approach you take, limiting REST API exposure to secured SSL and TLS channels is always a good idea. Avoid including sensitive credentials in API data payloads, URLs, or querystrings, as applications may store copies of these credentials inadvertently through automated logging procedures. Finally, because a manual approach may result in repetitive oversights and errors, automate procedures such as encryption key rotations.
The above are different ways how to make an api. API is a broader term, and REST API is a special kind of API that is popular with Cloud applications. The main focus of REST APIs is communication. REST APIs were presented to you in this post and while each of these methods has advantages of its own, they also add varying degrees of complexity, ranging from simple credential checking to proxy-controlled layers of permissions checking.

Digital Valley, 423, Apple Square, beside Lajamni Chowk, Mota Varachha, Surat, Gujarat 394101
D-401, titanium city center, 100 feet anand nagar road, Ahmedabad-380015
+91 9913 808 2851133 Sampley Ln Leander, Texas, 78641
52 Godalming Avenue, wallington, London - SM6 8NW